Thursday, October 21, 2021

As a small business owner, you know how powerful word of mouth is for attracting new customers. You also likely know how important it is to use social media platforms to help you spread the word–digitally. But did you know that brand engagement rates are highest on Instagram, beating both Facebook and Twitter? According to Instagram, 90% of its users follow at least one business.
How can you grow your Instagram followers and potential customer base — and keep your target audience coming back for more? In this article, you’ll learn why Instagram engagement matters, how to use the different features of the platform and tips and tricks for maximizing your reach and impact. We can help you set goals, set your Instagram account up for success and help you make the most out of your Instagram posts. Let’s dive in.
Set social media marketing strategy goals
Setting social media marketing strategy goals for your Instagram page can help you monitor the time, effort, and potential money you’re investing in marketing on platforms like Instagram.
Having clear Instagram engagement goals can help you plan and create content as well as monitor improvement. Marketing strategy goals can also help your team create quality content that aligns with what you aim to accomplish.
Set up a profile using Instagram for Business
Once you’ve set your goals, it’s time to start making your Instagram profile work for you. If your account is not set up as a business profile, consider switching to an Instagram for Business account. Using an Instagram for Business account provides benefits such as:
- Instagram analytics and tools that show how well your content is performing so you can track your goals more easily and understand your audience demographics and more.
- Features to expand your profile and sell products, including the ability to create and publish Instagram ads without having to use advertising tools through Facebook.
Creating a unique and on-brand Instagram page, in addition to high-quality content, can help you hook new followers by showing them why your business is worth following.
Create an Instagram bio that tells your story
While not directly tied to follower growth, your Instagram bio is your first opportunity to connect with potential followers and get them to click the follow button. The bio is a place to showcase your brand’s personality, tell visitors about your products or services and what makes it unique. An Instagram bio should include your company’s category/industry, your location(s), contact info and a link to your website. You also can include associated social media account handles.
There’s limited real estate to tell your brand’s story. With only 150 characters available, you need to keep it brief. You can use formatting to organize info in your Instagram bio, such as line breaks to create vertical spacing. If it makes sense for your brand’s voice, consider using emojis to show off your brand’s personality and potentially save character space. You could also use a call to action (CTA) in your bio to set up your profile’s link.
A profile photo can help potential followers instantly recognize that it’s your company. Most businesses use a logo, logomark (the logo without any words) or mascot as a profile photo. You could also use a photo of your sign or storefront–even an image of your signature products. Don’t feel like you have to limit your creativity, but make sure the image can easily identify your brand.
Use one clickable link to get followers to explore pages, content
Instagram offers one clickable link field in the bio for accounts with less than 10,000 followers. Your clickable link is prime real estate to send a potential customer where you’d like them to go. You can use the link to send people to your main website homepage or frequently change out the link to reflect an event you’re promoting or other current content you may produce.
Additionally, tools are available to create a “link in bio” link tree/landing page to offer multiple clickable links for Instagram posts, product pages and other links without leaving the Instagram app. This approach is best for businesses that have numerous offerings and want to drive customer traffic to multiple links or different types of content. No matter which strategy you use, you should use your clickable link to send Instagram users to visit other relevant content.
Create a visual identity and brand voice true to your business
Instagram is all about visuals, no matter the format. Maintaining a consistent visual identity that represents your brand can give your content a cohesive feel. This identity can include your brand colors, tones, and much more. Editing style, filters, and photo composition can all affect your visual identity.
A consistent and unique visual identity can help new followers get to know your brand by just seeing it. If you stay consistent, your Instagram audience will begin to associate the style with your brand unconsciously. No matter what content format you use on Instagram, your content should look like you and tell your brand’s story while adding value to your audience.
Your Instagram captions and text are just as crucial for brand storytelling and helping users find you.
You don’t want to focus solely on visuals, though. Having a brand voice for Instagram can allow you to experiment with all of the Instagram content formats and still consistently sound like your brand voice.
Does your brand use emojis? Will you make memes or repost memes? Does your brand voice use humor? As with visual identity, your brand voice can help your Instagram audience know it’s your business.
Use Instagram content formats to your advantage
Instagram began as an app to share photos. It is now a social media platform that continually releases new features and content formats for users to engage. The platform offers a variety of ways your business could interact with an engaged audience, including:
- Instagram Carousels: This feature allows for publishing up to 10 photos in a single post.
- Instagram Reels: This format, reminiscent of TikTok, hosts 15- to 30-second videos that can include audio, visual effects or other creative tools. Reels can be shared in your Instagram feed and discovered on the Instagram Reels tab on the platform.
- IGTV: Instagram TV, or IGTV, is for videos longer than 30 seconds. IGTV would be used best for a recurring video series.
- Instagram Stories: Stories are photos or videos that are full-screen, vertical and disappear after 24 hours. They appear at the very top of the app rather than in the news feed. The Stories feature is a good tool for visual storytelling, where you can produce things with a beginning, middle and end. Instagram Stories also can include fun, interactive elements such as stickers, polls and filters, which can increase engagement and get your audience in the habit of viewing your Stories consistently.
- Instagram Live: Instagram users can live stream video through Instagram Stories in this format. This format allows brands and content creators to connect directly with their followers and target audience through Q and A sessions, demonstrations and so much more.
- Instagram Guides: This content type is a cross between Instagram Carousels and blog posts. Each guide includes a cover image, title, introduction and optional descriptions for entries that users can build from previously posted content, places, or product listings from your account.
Post and interact with your audience consistently
Building an Instagram following requires posting regularly and interacting with your audience. That said, business owners need to sleep and take vacations. Consider using a tool that lets you schedule and publish Instagram posts, especially if you’re a team of one. There are a variety of tools available at different price points, such as Hootsuite, Sprout Social, Salesforce’s Social Studio and many more that can provide the functionality that meets your goals.
Instagram users expect a steady stream of interesting, engaging or educational content from the users and brands they follow. Having a consistent posting schedule shows your audience that you’re a serious brand worth following.
Responding to comments, mentions and direct messages (DMs) is also crucial for users to feel confident following your business. Your followers are real people with opinions, issues or questions, and responding and engaging shows respect. Additionally, make time to respond when someone mentions or tags your brand in their post –– they’re helping to spread the word about you! It’s easy for users to hit the unfollow button if they feel ignored; don’t let it come to that.
Additionally, you may want to consider developing social media guidelines to help the person managing the Instagram (if it’s not you) to help them navigate interactions with your Instagram followers.
Use hashtags to feed the Instagram algorithm
Hashtags help Instagram users find the content they want to see. Instagram hashtags are keywords or phrases with a hashtag symbol before them, such as “#photography.” Instagram captions are not searchable, but hashtags are. Clicking on a hashtag or searching for a specific hashtag will show users all content associated with that tag.
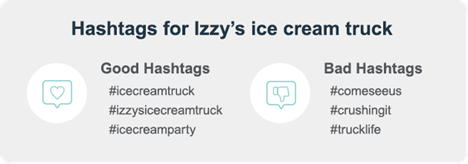
Hashtags can help improve the chances of potential followers finding and engaging with your content. Posts that contain a hashtag get more engagement than those without hashtags. Consider hashtags related to your business that are easy to use, catchy and popular for your posts. You can create a branded hashtag for followers to use when posting about your business.
Using broad hashtags related to your business increases the chance people see your posts from all corners of the world. You may also want to use branded hashtags that are unique to your business to capture more local/relevant attention. If a hashtag is irrelevant to your post, it will not make sense to potential followers or aid your goals.
Help users find you with geotags
Geotags, or Instagram location tags, use a precise location that users can add to a post or Story. The tags can be identified by the GPS in a mobile device and can be geographical (like a city) or a particular business (think like a restaurant). Businesses can create a geotag for their business and start reaping the benefits of using it on posts.
Using geotags helps Instagram compile posts tagged at the location. A geotag can be added at the time of posting or retroactively. Instagram categorizes posts as “top” and “recent” posts by location, and your brand photos will live among the posts from your customers or visitors when they use a geotag while posting about or from within your business.
The “View Information” button within the geotag can link to information about the business. The geotag functions can help with brand awareness and allow potential customers to research your business and see what others have posted about you.
Promote your Instagram on other social media channels
If you have an engaged following on other social networks, let them know you’re on Instagram. Let them know what kind of content you’ll be posting – that way, they can decide if it’s worth their time to follow you in multiple locations. Additionally, use Instagram stories and crosspost them to your Facebook page to help you reach new audiences and increase the likelihood you’ll get the follow on Instagram.
Grow your reach with Instagram ads and campaigns
Instagram ads can get your content in front of a broad, targeted audience and help you reach your goals faster. You can “boost” your social posts to a wider audience or create specific advertisements for products or services. Instagram ads increase the reach of your content as well as include call-to-action buttons. These features help reduce the steps to get viewers to your website or store from the app.
You can buy Instagram ads through their platform. You set a maximum budget of what you’d like to spend for the entire time the ad runs. Costs for Instagram ads can average around $.50 to $1 per click, or cost per click (CPC). You can try out Instagram ads with a small budget and track the insights to see if it’s the right strategy for your business. It can be an effective and targeted way to reach prospective customers in the right stage of their buyer journey.
Consider working with influencers
Influencer marketing is a great way to build a loyal Instagram following. Instagram influencers are basically people who post a lot of content and have a lot of engaged followers. Influencers often work with brands and businesses to help generate interest in their products and services.
The thought of influencer marketing can seem intimidating to smaller businesses but consider working with micro-influencers: content creators with a smaller but dedicated following, often in local markets or within specific categories like food, crafts, etc. Look for popular content creators within your industry with small or large followings that might be interested in your brand.
Think about your own Instagram follower customer base. You could already have an influential (or budding) brand ambassador following you – consider making a collaboration official. The more genuine the relationship between a brand and influencer, the better.
They found you on Instagram – now deliver the great experience you showed them
Instagram growth for your business doesn’t need to be scary or a herculean effort.
With the right resources and planning, you can achieve your marketing goals with new followers and more. After all, it’s about your brand’s ability to connect with real people and showing them great content about what you do best: provide great products or services.
At Heartland, we love helping businesses succeed –– online and offline. That’s why we offer training and resources like our free Unstuck Playbook. This training walks you through easy and effective strategies to get your business from surviving to thriving. We also offer solutionsranging from payments and point of sale to customer engagement and employee management to help entrepreneurs focus on the big picture of their business.




